In the contemporary landscape of financial transactions, UPI (Unified Payments Interface) payment applications have evolved to become indispensable tools, streamlining monetary transfers, bill payments, and retail transactions through the seamless integration of smartphones. Nevertheless, this newfound convenience must be accompanied by a comprehensive comprehension of the vital component of UPI payment app security.
Picture your UPI app as a secure vault, diligently safeguarding your financial assets. In essence, UPI payment app security aspires to fortify this virtual vault against external threats and breaches, assuring the sanctity of your financial data.
This discussion shall embark on an exploration of the intricate mechanisms that constitute UPI payment app security. We shall delve into encryption, akin to an intricate cryptographic code, reinforcing the confidentiality of your data.
Additionally, we will scrutinize diverse authentication techniques and the incorporation of two-factor authentication, contributing to a nuanced understanding of these security measures, and ultimately facilitating your informed and secure navigation of digital financial transactions.
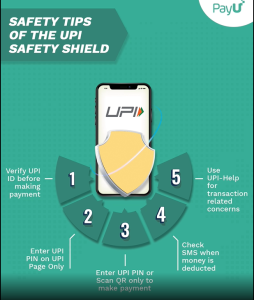
The Importance of Security in UPI Payment Apps
Security in UPI payment apps is of paramount importance for several reasons:
- Financial Protection: UPI apps deal with sensitive financial data, including bank account details and transaction history. Robust security measures safeguard this information from unauthorized access and financial fraud.
- User Trust: Ensuring the security of UPI transactions builds trust among users. When people trust these apps, they are more likely to use them for everyday financial activities, boosting their adoption and usefulness.
- Data Privacy: UPI apps handle personal and financial information, and privacy breaches can lead to identity theft and financial losses. Adequate security safeguards users’ data privacy.
- Regulatory Compliance: Regulatory authorities require UPI apps to adhere to stringent security standards to protect users and maintain the integrity of the financial system.
- Cyber Threats: The digital landscape is rife with cyber threats like phishing, malware, and hacking. Strong security measures help thwart these threats, preventing unauthorized access and financial losses.
Foundations of Encryption and Data Protection
Encryption is a core element of cybersecurity and data protection, involving complex algorithms and encryption keys to render data unreadable without the right decryption key. It safeguards sensitive information from unauthorized access and interception.
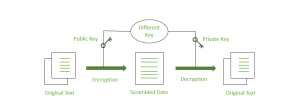
There are two primary encryption types:
- Symmetric Encryption: Uses a single shared key for both encryption and decryption. While efficient, secure key exchange is vital.
- Asymmetric Encryption: Employs a public key for encryption and a private key for decryption. It’s more secure in key distribution but can be computationally intensive.
Data protection, on the other hand, encompasses measures to safeguard data integrity, confidentiality, and availability. Key aspects include access control, encryption, regular backups, data retention policies, security training, and compliance with data security standards and regulations.
The Use of Encryption Protocols
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are critical for online security. They begin by verifying a website’s identity using digital certificates from trusted authorities, ensuring you’re connecting to a legitimate source.
Once confirmed, SSL/TLS encrypts your data during transmission, making it unreadable to unauthorized parties. They also verify data integrity by adding a unique fingerprint and detecting any tampering during transit.
A noteworthy feature is forward secrecy, generating unique encryption keys for each session, preventing past data from being compromised in the event of a future server breach.
SSL/TLS are versatile and protect various online services, including web browsing, emails, and file transfers. They enhance trust in e-commerce with indicators like the padlock symbol and “https://,” and they ensure compliance with data protection regulations, instilling confidence in handling sensitive data.
Protection of Data
- Data in Transit: Data in transit is secured through encryption and secure communication protocols like SSL/TLS. Encryption converts data into an unreadable format during transmission, while secure protocols create safe channels for data transfer, ensuring confidentiality and integrity. User authentication further prevents unauthorized access.
- Data at Rest: Data at rest is protected through encryption, access controls, data backups, data deletion practices, and physical security measures. Encryption renders stored data unreadable without decryption keys, access controls limit data access, backups ensure recoverability, secure deletion prevents data breaches, and physical security safeguards against unauthorized access and damage. Data classification guides the application of appropriate security measures.
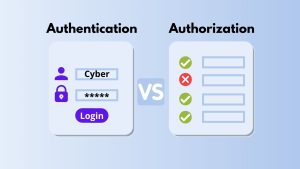
Authentication and Authorization in Cybersecurity
Authentication and authorization are two fundamental concepts in the realm of cybersecurity and access control, each serving a distinct yet interconnected role in ensuring the security of systems and data.
Authentication
Authentication is the process of confirming the identity of a user or system. It ensures that the entity attempting access is who it claims to be. This can involve usernames and passwords, biometrics, multi-factor authentication (MFA), or digital certificates.
Authorization
Authorization follows authentication and determines what actions an authenticated entity is allowed to perform. It sets permissions and rules based on roles or attributes, ensuring that users or systems can only access and interact with resources and perform actions they are explicitly permitted to do.
User Authentication Methods
- Username and Password: This traditional method involves users providing a unique username and a secret password for access. Its effectiveness relies on the strength and confidentiality of passwords.
- Multi-Factor Authentication (MFA): MFA enhances security by requiring users to provide two or more authentication factors. Common factors include something they know (password), something they have (a smartphone-generated code or a hardware token), and something they are (biometrics).
- Biometrics: Biometric authentication uses distinctive physical or behavioral attributes such as fingerprints, facial features, or voice patterns for identity verification. It offers a high level of security but often requires specialized hardware.
- Smart Cards and Tokens: These methods involve the use of physical devices, such as smart cards or tokens, to generate one-time or time-based codes for authentication.
- Certificate-Based Authentication: Digital certificates, issued by trusted authorities, validate the identity of users or systems. Authentication is accomplished by presenting certificates and their corresponding private keys.
Authorization Mechanisms
- Role-Based Access Control (RBAC): RBAC assigns users specific roles, each with predefined permissions. Users are granted access based on their assigned roles, simplifying access management.
- Attribute-Based Access Control (ABAC): ABAC considers various attributes like user characteristics, resource properties, and environmental factors to make access decisions. This approach provides fine-grained access control.
- Rule-Based Access Control: Rule-based access control employs predefined rules to determine access. Rules can be based on specific conditions, like time of day or user location.
- Mandatory Access Control (MAC): MAC enforces strict access control based on security labels, typically used in high-security environments such as government agencies.
- Discretionary Access Control (DAC): DAC allows resource owners to control access to their resources. Owners can grant or revoke access permissions as needed.
- Policy-Based Access Control: Policy-based access control relies on predefined policies to determine access rights. These policies define who can access what resources under specific circumstances.
Fraud Prevention Measures
- Identity Verification: Strong identity verification processes ensure that individuals are who they claim to be, reducing the risk of identity theft.
- Transaction Monitoring: Continuous monitoring of financial transactions helps identify suspicious patterns or anomalies in real-time.
- Data Encryption: Encryption protects sensitive information during transmission and storage, preventing unauthorized access.
- Machine Learning and AI: These technologies detect patterns and anomalies indicative of fraudulent behavior, improving accuracy over time.
- Biometric Authentication: Biometrics, like fingerprints and facial recognition, provide highly secure user verification.
- Employee Training: Educating employees on security risks and fraud prevention helps in recognizing and mitigating threats.
- Regular Software Updates: Keeping software up to date is essential to patch vulnerabilities that fraudsters may exploit.
- Customer Education: Educating customers about common fraud schemes empowers them to recognize and avoid potential threats.
- Incident Response Plan: Having a well-defined plan in place enables swift responses to fraud incidents, minimizing damage.
Fraud Detection Techniques
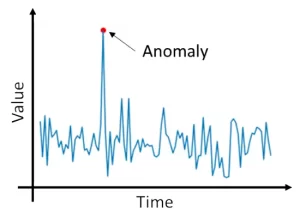
1. Anomaly Detection
Anomaly detection is a method focused on identifying deviations or anomalies in data that do not conform to established patterns, to detect potentially fraudulent activities. This technique relies on the following principles:
- Statistical Models: Anomaly detection often utilizes statistical models to establish a baseline of normal behavior. Any data points that significantly deviate from this baseline are considered anomalies.
- Unsupervised Learning: This technique employs unsupervised learning algorithms to automatically identify irregular patterns or outliers in data without relying on predefined labels.
- Threshold-Based Detection: Sometimes, simple threshold-based rules are applied to flag data points that fall beyond predefined limits as anomalies.
- Time-Series Analysis: For sequential data, such as financial transactions, time-series analysis is employed to identify abnormal trends or sudden deviations over time.
Anomaly detection is advantageous for its ability to detect novel and previously unseen fraud patterns, providing adaptability to evolving fraud tactics.
2. Machine Learning
Machine learning plays a pivotal role in fraud detection, offering automation and adaptability. Here’s how it contributes:
- Supervised Learning: In supervised learning, models are trained on labeled data that includes both fraudulent and legitimate instances. These models learn to classify new data based on patterns extracted from the training data.
- Feature Engineering: Feature engineering involves selecting and transforming relevant data attributes to distinguish fraudulent from non-fraudulent activities. Features may include transaction amount, location, and time.
- Ensemble Methods: Ensemble methods combine multiple machine learning models to enhance accuracy and robustness in fraud detection.
- Deep Learning: Deep learning techniques, such as neural networks, are used to identify intricate patterns and sophisticated fraud schemes in complex datasets.
- Real-Time Scoring: Machine learning models can be deployed for real-time scoring, allowing instant fraud detection and prevention during transactions or interactions.
Transaction Monitoring
Transaction monitoring serves as a vigilant guardian in the realm of financial security, especially for businesses and financial institutions. Its primary purpose is to systematically track and analyze financial transactions, aiding in the early detection of suspicious or fraudulent activities. Here’s how it operates:
- Comprehensive Surveillance: Transaction monitoring comprehensively observes all financial transactions within an organization, whether they involve online purchases, fund transfers, or in-store card swipes.
- Anomaly Detection: It functions as an anomaly detector, continuously evaluating transaction data against established patterns and historical behavior. Deviations from the expected norm are flagged for further investigation.
- Rule-Based Alerts: Organizations can establish predefined rules and conditions that indicate potentially suspicious activity. For instance, if a single credit card is used for multiple high-value transactions within a short time frame, the system can trigger an alert.
- Machine Learning Integration: Some advanced transaction monitoring systems leverage machine learning techniques, enabling them to adapt and learn from historical data. This allows them to identify novel and previously unseen fraud patterns.
- Real-Time Response: One of its significant advantages is real-time operation. When it identifies an anomaly or suspicious activity, it can trigger immediate responses, such as blocking a transaction or notifying security personnel.
- Continuous Operation: Transaction monitoring systems operate 24/7, ensuring continuous vigilance regardless of the time or day. This persistent surveillance is crucial in promptly addressing potential threats.
Regulatory Compliance
In the corporate sphere, regulatory compliance assumes the role of a comprehensive playbook that organizations must adhere to, ensuring equitable and responsible conduct. This framework comprises a wide array of rules and directives instituted by governmental bodies and regulatory authorities, encompassing domains such as financial reporting, data safeguarding, consumer protection, environmental stewardship, and more.
To preserve the bedrock of trust and integrity within the financial sector, businesses and financial institutions find themselves navigating a complex labyrinth of regulations. They are obliged to align with the exacting standards established by authoritative bodies, such as the Reserve Bank of India (RBI), and industry-specific benchmarks exemplified by the Payment Card Industry Data Security Standard (PCI DSS).
RBI, in its capacity as the sentinel of India’s financial landscape, exerts substantial influence. It promulgates regulations governing critical facets, including payment systems, anti-money laundering (AML) protocols, and know-your-customer (KYC) practices. These measures are diligently crafted to ensure the execution of financial transactions with unwavering integrity and security, preempting any encroachments by fraudulent activities.
On the international stage, PCI DSS assumes prominence, centering its efforts on the impervious protection of payment card data. Organizations entrusted with the custodianship of payment card information are bound by exacting stipulations, mandating robust encryption, meticulous access controls, and periodic security assessments.
Sustaining regulatory compliance is not a transient endeavor; it embodies an enduring commitment. This commitment entails a perpetual cycle of activities, comprising routine audits, scrupulous risk assessments, and exhaustive security training for personnel. Maintaining abreast of evolving regulations and expeditiously effecting requisite adaptations stands as a cardinal imperative.
In essence, compliance transcends mere adherence to rules; it is a tenet that fortifies the foundation of trust in the financial realm. It serves as the guardian of the interests of financial institutions and the populace they serve, fostering a realm where principles of integrity and responsibility preside.
Best Practices for Secure Coding and Development
Consider these practices as the architectural blueprint for constructing a resilient and secure edifice:
- Input Validation: Scrutinize all external inputs rigorously, guarding against common attacks like SQL injection and cross-site scripting (XSS). Data must be sanitized and validated before processing.
- Authentication and Authorization: Robust authentication mechanisms and meticulous authorization controls ensure that only authorized individuals gain access to critical resources, protecting against unauthorized breaches.
- Data Encryption: Encrypt sensitive data at rest and in transit using robust encryption algorithms. Safeguard encryption keys with stringent security measures.
- Error Handling: Develop comprehensive error-handling mechanisms that reveal minimal information to potential attackers, thereby thwarting potential threats.
- Security Libraries and Frameworks: Leverage established security libraries and frameworks to handle security-related tasks, reducing the likelihood of vulnerabilities.
- Least Privilege Principle: Adhere to the principle of least privilege, ensuring that individuals and processes are granted only the permissions necessary for their designated roles, thus minimizing the attack surface.
- Secure Configuration: Configure all components, including servers and databases, with security as the paramount consideration. Disabling unnecessary services, altering default passwords, and ensuring software updates are vital aspects.
Code Reviews, Penetration Testing, and Security Audit
These activities serve as vigilant guardians, consistently evaluating the security measures in place:
1. Code Reviews
Comparable to meticulous inspections by experts, peer code reviews are conducted to identify vulnerabilities, coding errors, and design flaws. They encourage collaboration and knowledge sharing among development teams.
2. Penetration Testing
Penetration tests simulate real-world attacks, scrutinizing the digital fortress for vulnerabilities. This process helps assess the effectiveness of security controls and prioritizes remediation efforts.
3. Security Audits
Comprehensive security audits encompass code reviews, system configurations, access controls, and compliance with industry standards and regulations. They provide an overarching evaluation of an organization’s security posture.
Conclusion
In summary, security constitutes the foundational pillar of UPI payment app development, representing an indispensable requirement rather than a discretionary consideration. In an era characterized by the ubiquity of digital transactions, the protection of user data and the establishment of trust stand as imperative objectives. Through the diligent implementation of robust security measures encompassing encryption, stringent authentication mechanisms, vigilant real-time monitoring, and unwavering adherence to regulatory standards, developers can craft
UPI payment apps not only offer user-friendly experiences but also excel in terms of resolute security. Security should not be perceived as an impediment but rather as the linchpin that unlocks the full potential of these apps within an ever-evolving digital landscape. Ultimately, the triumph of UPI payment apps hinges upon their capacity to deliver seamless usability while concurrently assuring users of the highest degree of data security, positioning security as an integral and non-negotiable facet of their developmental trajectory.